Ensuring your data is available after malware or a disaster is easier than you think. Start with backup strategy fundamentals.

3-2-1 backup rule is the standard for the minimum amount and types of backups that all companies should have deployed. If you are asking yourself where to start with backups then this is the perfect place to start. Future blogs will go into different software, hardware, and locations, but for now, we will focus on establishing the basics so you can start to fill in the blanks on your backup plan. If you are still worried about where to start, reach out to Secure Packet today as we provide DR services along with IT consulting services to ensure you are following best practices.
Whether you are backing up server data, customer data, or employee data, the rules are the same in terms of the 3-2-1 rule. If you are under any type of compliance, such as HIPAA, PCI-DSS, SOC, etc, then you will have to have at least the 3-2-1 rule for your backups. The Cybersecurity and Infrastructure Security Agency (CISA) recommends that all individuals and businesses use the 3-2-1 rules for backups.
What is the 3-2-1 Backup Rule exactly?
To increase your chances of recovering lost or corrupted data, CISA states that you should:
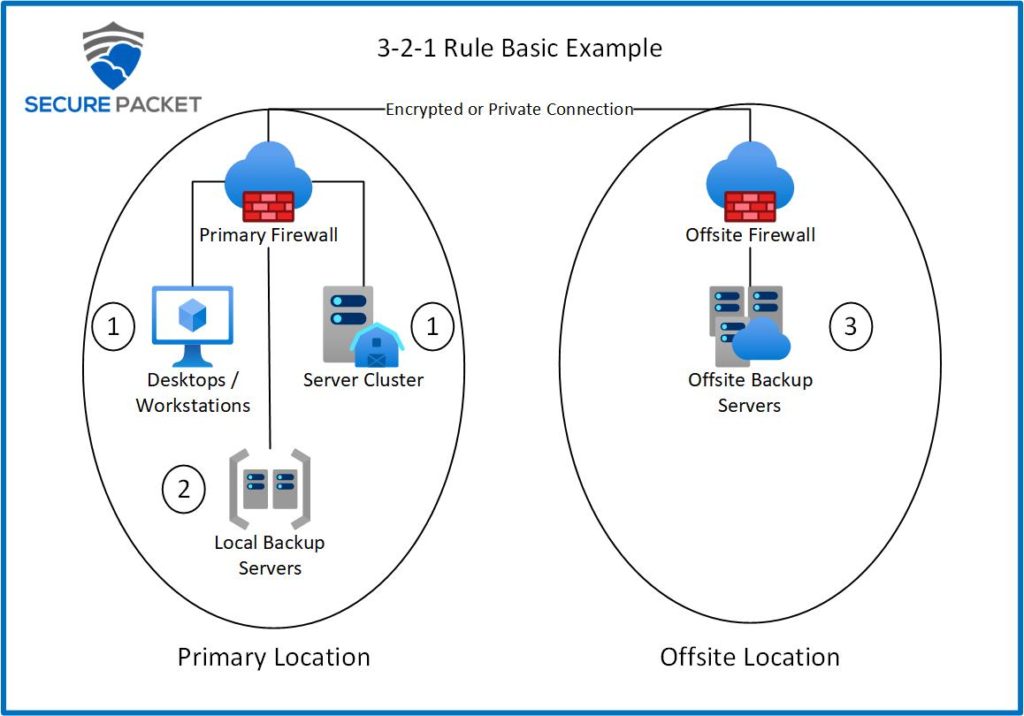
3 – Keep 3 copies of any important file: 1 primary and 2 backups.
2 – Keep the files on 2 different media types to protect against different types of hazards.
1 – Store 1 copy offsite (e.g., outside your home or business facility).
The first “copy” of data that the rule refers to is the “live” data that is currently being used on the server or workstation. This is the primary data and will be interacted with on a daily basis. The other two copies are backups and are not interacted with by any other system or user outside of your backup software.
Storing the data on two different media types is dependent on how your systems will be storing the data. The biggest takeaway from storing your data on two different media types is to understand that having backups on the same drive as your primary data is a non-starter. The same goes for keeping another hard drive in your computer or server just for backups as server failures happen just often enough for this to be considered extremely risky. Physical removal of backup drives or tape drives in a daily, weekly, or monthly rotation has become mostly obsolete due to larger bandwidth between sites, however, for companies on extreme budgets, this can still be an option. Most small businesses will opt for either a daily or weekly rotation of storage media in their backup solution. Software offerings like Veeam, for example, have been updated for options that fit all size business needs so be aware that there is a solution out there for your needs.
Off-Site Backups
Keeping at least one copy offsite at a remote location is a must. Whether the concern during your company’s risk analysis is fire, flooding, hurricanes, riots, or anything else that can cause loss of your computer room and all your systems, having your data offsite so you can restore from the backups is a must. What would happen to your business if you suddenly lost all of your customer data due to an employee error or malware attack? How would you recover if all of your data onsite is now encrypted? Having that offsite copy is absolutely critical in ensuring your business will recover.
You might be asking yourself, “How can I lose my data?”
Our team has compiled a list of what they have seen and some reasons might be reasons you didn’t think about.
- Storage Failure – Hard drive (HDD), solid-state disk (SSD), or more advanced SAN, NAS, or RAID arrays do fail and will fail with enough time. Remember that RAID is not a backup.
- Ransomware attacks have been on the rise for the past 5-10+ years and they are not slowing down. The type and way they attack constantly change, but payment via crypto is one example of how attackers change the way they operate.
- A localize disaster – whether there is a lightning strike, flooding, riots, fire, hurricane, tornado, or anything else that could destroy your computer systems these rank lower in chances while still happening to companies every day.
- Bad Actor Employee – This would be an employee who is angry at the company or if your employee simply wants to steal the data to use for their own personal gain.
- Human error – this can range anywhere from a mistake on maintenance to the system, a janitor being careless, an employee forgetting to perform certain monitoring tasks, or a host of all types of reasons we have seen through the years. The less human interaction with your systems the better.
Next Steps – Ensuring Backups are always available
This all seems pretty basic once you break it down and at this point of your backup plan, it should be. The hardest part of the 3-2-1 rule is simply being aware and ensuring your backup plans meet the 3-2-1 minimum requirements along with making sure those minimums fit your company’s needs. Now that you know the basics of the 3-2-1 rule, do you meet the minimums?
If you need some help to ensure that your backup plans are exceeding your needs, reach out to Secure Packet today as we offer IT Consulting services. Also, Backups and Disaster Recovery are key consulting areas for Secure Packet as they are a critical need for all businesses. We are able to help the smaller 1-5 employee businesses all the way up to the 1,000+ employee enterprises to ensure all restore point objectives and restore time objectives will be met if you ever have to utilize your backups. Contact Secure Packet today!
