Understanding the difference between RTO and RPO
Whether you are a C-level executive looking to ensure that your company’s DR plan is up to spec or if you have been tasked with ensuring your company’s ability to restore from a malware attack or a disaster then RTO and RPO are essential when reviewing and testing your backup and restore plans that are critical pieces of your disaster recovery plans. If you are unsure about the 3-2-1 Rule, take a second to read this blog to ensure you understand the different pieces of a backup that is required for a successful business backup plan. If you need help with your DR plan, Secure Packet offers IT Consulting services to ensure your plan follows all best practices along with fitting within your budget.
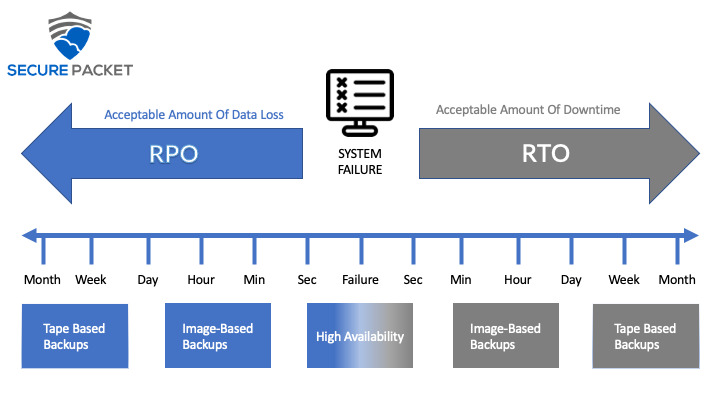
What is RTO?
RTO stands for recovery time objective. RTO is referring to how long would it take to go live with your backup solution. For most backup solutions, this is referring to how long would it take to declare a disaster has occurred and a backup has to be restored. Then add in the time that it would take to transfer your backup data files to a live production server and for that server to become officially live and serve traffic again. When reviewing DR (disaster recovery) plans with clients, most have not factored this time frame into business continuity plans (BC plans). RTO has become more and more important as companies rely on teams’ access to files and data, whether working remotely or from the office. In the early 2000s to early 2010s, it wasn’t as big of an issue since the file sizes were not as large or databases were smaller, however, now data lakes have become a norm even for small and medium businesses. The days of relying on a 1 Gbps connection for backups are now being phased out for 10 Gbps, 25 Gbps, or even 100 Gbps connections between systems. Veeam and other backup software have been updated throughout the years to ensure they can fully utilize these larger connections.
Examples of RTO times and connections
Below are some examples of what to expect with restore times for different common file sizes and connections. You can use a data transfer calculator found here so you can see what your data sizes would take with different connection speeds. Keep in mind that a 1 Gbps Ethernet connection would only provide you roughly 880 Mbps in the real world as long as your CPU, RAM, and Disk speeds are up to the task of the transfer as well. All components of your servers, firewalls, interconnects, and internet or private connections for off-site backups play key parts in your transfer speeds. It is a must to test out all restore plans to ensure your restore times and speeds meet your RTOs. One single component can be the bottleneck that will bring your restore to a crawl.
| Example Data Source | Connection Type | Approx. Restore Time |
|---|---|---|
| 10 GB DB | 1 Gbps | 2 Minutes |
| 400 GB VM | 1 Gbps | 1 Hour |
| 10 TB VM w/ DB | 1 Gbps | 24 Hours |
| 80 TB Data Lake | 1 Gbps | 200 Hours (almost 8 days) |
| 10 TB VM w/ DB | 10 Gbps | 2.5 Hours |
| 80 TB Data Lake | 10 Gbps | 18 Hours |
| 80 TB Data Lake | 100 Gbps | 2 Hours |
What is RPO?
RPO stands for restore point objective. RPO is referring to the point in time that you would be restoring to since the last successful backup was completed. For example, most static websites are backed up once a day or referred to as daily backups. If you configured your backup systems for a daily backup, then your backup systems would perform the backup job once a day. When a disaster is declared or you need to restore some files from your backup, then your backup would most likely not be older than 24 hours.
The question for you and your business disaster plan pertaining to RPO is what amount of data are you able to lose and whether that data loss is acceptable to your business. Most C-level executives would say that they want zero data loss. Most people when asked would say the same thing until you start to evaluate the costs to an SMB company when applying that level of zero data loss to your entire server and IT stack.
Examples of RPOs
Here are some recommendations to RPOs for different types of servers and workstations. Please keep in mind that all businesses are different with different operational and compliance requirements.
| Data Source | Suggested RPO | Notes |
|---|---|---|
| Blog | Daily | A no-revenue or small revenue-generating site requires minimal backup usually due to budget |
| Static Business Website | Daily | Very few changes occur so a Daily backup usually fits great for infrequent changes. |
| Customer Created Data Website | Hourly and Daily | Customer-created data like videos, music, photos can be unreplaceable so ensure your backup plan fits the need |
| Inventory or Order-Based Website and Database | 5 minute, 15 minute, and/or hourly, with Daily Backups with long-term retention | Do any PCI-DSS or any other compliances need to be accounted for? |
| Financial Database | HA, Constant Backup, Hourly, and Daily with long-term retention | Any PCI-DSS and other Fintech compliance should be accounted for |
| HIPAA Patient Database | HA, Constant Backup, Hourly, and Daily with long-term retention | HIPAA compliance and possible HITRUST compliances should be accounted for |
Where does the retention of backups come into play?
One part of your disaster recovery plan that is discussed but not always included in RPO and RTO is the retention of these backups. If you only have 1 retention point or a handful, then in the case of malware and hourly backups, do you have enough retention points to revert prior to the infection? Most locking crypto-malware is now crafted to either lock immediately or stay dormant for a certain period of time. Most wait longer than 30 days due to that being the normal retention period of backups. Essentially means that the crypto locker malware can be restored with your oldest retained backup and then in another 30 days or so, this crypto locker backup will again lock your data while causing more downtime.
Do you know what the best practices are for a business like yours?
If you are unsure or just want a second set of eyes for your disaster recovery plan, Secure Packet is here to help review your business requirements, budgets, and overall IT plan to ensure that your business can not only survive but recover quickly from any type of disaster or malware attack. Whether you select Secure Packet or another IT service provider, ensure that you are very clear on your company’s operational requirements, compliance requirements, and any guarantees or SLAs that you have entered into with your clients. With this type of information, you and your service provider can craft the ideal backup and disaster recovery solution to fit your needs.
Looking for some help and guidance on what the next step is for your disaster recovery plan? Secure Packet engineers are standing by to help. Schedule a free call today to ensure you are covered.
